Wednesday 1 April, 2009, 05:30 - Radio Randomness
Posted by Administrator
For some time, there has been software available on the internet which would allow anyone with enough brains and patience to hack into a 'WEP' encrypted WiFi link. 'WPA' encrypted links are more secure but even they are open to hacking. The basic problem with such devices is that they transmit the data freely across the ether and if a miscreant within range has the right equipment and software they can intercept the radio signal and decode it. Be sure though that it takes a lot of effort, someone would really have to be serious in order to bother having a go at WPA and WPA2.Posted by Administrator
 But regardless of the encryption technology used, the key problem with any WiFi network is that the signal is purposefully transmitted over a wide area. Obviously running a direct wired connection between two points is much more secure. Surprise, therefore, may be expressed at the realisation that even the radiation from computer keyboards can be sufficient to allow 'snooping' on your computing activities from a distance.
But regardless of the encryption technology used, the key problem with any WiFi network is that the signal is purposefully transmitted over a wide area. Obviously running a direct wired connection between two points is much more secure. Surprise, therefore, may be expressed at the realisation that even the radiation from computer keyboards can be sufficient to allow 'snooping' on your computing activities from a distance. Two Swiss scientists have proven that this can be done, even through a wall, despite the fact that the levels of radiation coming from the keyboard are very small indeed.
But what about the new PLT (power line telecoms) or BPL (broadband over power line) technologies. These devices send your precious data over electrical cables which, any number of studies have shown, leak the signal hither and thither, causing both radio interference over a wide area and opening up the opportunity for someone to intercept the signal.
Some PLT/BPL devices have been received at over 500 metres from the building in which they are installed, which is, in most cases, further away than it would be possible to receive an equivalent WiFi signal. Wireless Waffle therefore decided to follow in the footsteps of the hitherto mentioned Swiss scientists and see whether or not it was possible to intercept and decode emissions from these devices in order to try and ascertain how secure they are or aren't.
 The devices which seem to send out the greatest signal are those manufactured by a company called Comtrend, and which use the chipset from another company, DS2. The first thing to do, therefore, was to get hold of a Comtrend device and modify the circuitry to make a seperate antenna input rather than the device looking for the signal on the mains cable to which it is attached.
The devices which seem to send out the greatest signal are those manufactured by a company called Comtrend, and which use the chipset from another company, DS2. The first thing to do, therefore, was to get hold of a Comtrend device and modify the circuitry to make a seperate antenna input rather than the device looking for the signal on the mains cable to which it is attached.A suitable Comtrend device was purchased from the web's best know outlet of all things slightly dodgy which was then dismantled to see where the signal input is. It turns out that the device sniffs the signal from the mains through a couple of high voltage capacitors. It is a straightforward job, therefore, to lift these capacitors from the circuit board and attach an alternative signal feed.
Making a wideband antenna capable of receiving the whole HF frequency range (2 - 28 MHz) used by these devices is not necessarily straightforward, however a short whip (1m or so long) connected directly to the input of a high-impedance FET amplifier does a pretty good job and whilst the response isn't necessarily flat across the HF range it does a reasonable job of receiving something at all frequencies. And, let's face it, the frequency response of the mains cabling to which the devices are normally connected is not flat either so a bit of loss here and there shouldn't be anything to worry about.
So, armed with an inverter (to provide the Comtrend device with 240V from the DC power outlet in a car which was felt easier than supplying it with the various DC voltages it needed), a laptop with which to connect to the modified device and a whip antenna, the intrepid Wireless Waffle team set off to see whether or not it is possible to intercept data being sent over electrical mains wiring and thereby spy on local internet activity.
The first test was to set up a couple of devices in a known configuration and then put the 'interception' kit inside the house in which the devices were installed. This gives the set-up the maximum possible chance of receiving the data as the signal received on the antenna within the house as pretty much as strong as it is on the mains wiring itself!
Not surprisingly, in such an 'ideal' test set-up it was a piece of cake to read the data passing over the mains cabling.
 Next, the interceptor was moved to a car parked outside the house with a suitably covert antenna placed secretly on the roof. Again, it was easy to receive and read the data being sent over the mains cabling. If it were me using these devices in my house, this is the point that I would begin to realise that the devices are not even as secure as WiFi, and would get rather nervous. The car was then driven 100 metres away from the house under test whilst keeping the system turned-on. At this distance, the signal from the house had fallen significantly (though was still perfectly audible on a test receiver).
Next, the interceptor was moved to a car parked outside the house with a suitably covert antenna placed secretly on the roof. Again, it was easy to receive and read the data being sent over the mains cabling. If it were me using these devices in my house, this is the point that I would begin to realise that the devices are not even as secure as WiFi, and would get rather nervous. The car was then driven 100 metres away from the house under test whilst keeping the system turned-on. At this distance, the signal from the house had fallen significantly (though was still perfectly audible on a test receiver).  At this distance, the simple interceptor spy-tool-device struggled to read the signal, however with some judicious placing of the receiving aerial, some of the data could be read. With such a simple set-up, not a great deal was really expected, however the tests proved PLT/BPL devices to be significantly less secure than WiFi being easy to intercept at distances of up to 100 metres from a house in which they are installed using very simple equipment.
At this distance, the simple interceptor spy-tool-device struggled to read the signal, however with some judicious placing of the receiving aerial, some of the data could be read. With such a simple set-up, not a great deal was really expected, however the tests proved PLT/BPL devices to be significantly less secure than WiFi being easy to intercept at distances of up to 100 metres from a house in which they are installed using very simple equipment. Unlike WiFi, however, it is not as easy to make a 2-way connection: whilst intercepting or spying on data is possible, completely hacking the connection and being able to use it, for example to connect to the internet or into a home network, is much more difficult. Generating enough transmitter power to put a strong signal on the internal mains wiring from 100 metres away would be no mean feat. That doesn't mean that it's not worth trying though...
1 comment
( 2834 views )
| permalink
| 



 ( 2.7 / 22938 )
( 2.7 / 22938 )




 ( 2.7 / 22938 )
( 2.7 / 22938 )
Thursday 12 March, 2009, 09:00 - Licensed
Posted by Administrator
Posted by Administrator
 Have you ever tuned into your local radio station and heard the travel news being read out from the 'eye in the sky' - a presenter checking out the traffic from an aircraft high over the area concerned? Have you ever stopped to think how that is done? Well Wireless Waffle is here to help explain it all.
Have you ever tuned into your local radio station and heard the travel news being read out from the 'eye in the sky' - a presenter checking out the traffic from an aircraft high over the area concerned? Have you ever stopped to think how that is done? Well Wireless Waffle is here to help explain it all.There is no denying that it would be very easy for any radio station to pretend to have a traffic plane or helicopter by playing sound effects in the background whilst the travel news was read out. However, there are some real benefits about doing it properly, not least it is possible to find out how the traffic is flowing as and when problems occur instead of waiting for listeners to phone in news (which can be unreliable) or for the local police or traffic department to let you know what's happening. But that doesn't mean that the aircraft in question can necessarily see all the problems in an area and in some cases, it is not possible to fly over certain areas due to airspace restrictions (for example, it would not make sense for a 'traffic plane' to be buzzing around a major airport, stopping commercial airliners from landing!)
What happens, therefore, is that there is someone on the ground who collates traffic information in the normal way (eg through listeners or the police) and then relays this information to the man in the aircraft. The plane (or chopper) can then visit some of the travel hotspots and see what is happening and if, along the way, they see other problems that haven't been reported, they can update the person on the ground. This means that, in general, travel news from an aircraft is more accurate and up-to-date than travel news from a regular travel studio.
From the technology perspective, there is lots of radio used (hence the Wireless Waffle interest). For starters, the pilot will be communicating with various air traffic controllers on the VHF aeronautical band (117.975 to 137.000 MHz).
 Next, there is a need for the person on the ground, including the presenter in the radio studio, to be able to communicate with the presenter in the aircraft - the 'uplink'. Typically this is done via a simple VHF or UHF PMR frequency (in the UK try listening around 141.000 to 141.500 MHz and 455.000 to 455.500 MHz). As well as passing travel news to the airborne presenter, this frequency is also often used as the 'cue', providing a live feed of the station on which the travel news is to be broadcast so that the airborne presented knows when to start reading the news.
Next, there is a need for the person on the ground, including the presenter in the radio studio, to be able to communicate with the presenter in the aircraft - the 'uplink'. Typically this is done via a simple VHF or UHF PMR frequency (in the UK try listening around 141.000 to 141.500 MHz and 455.000 to 455.500 MHz). As well as passing travel news to the airborne presenter, this frequency is also often used as the 'cue', providing a live feed of the station on which the travel news is to be broadcast so that the airborne presented knows when to start reading the news.Finally there is a the link from the airborne presenter to the ground - the 'downlink'. This is usually (but not always) a slightly higher quality link than the uplink as the audio is going to be broadcast. In the UK, these links are usually at UHF (try between 467.250 and 469.900 MHz). As they are transmitted from the aircraft, despite being low power, they can often be heard over a wide area.
If the aircraft is providing travel news for a wide area, more than one up and/or downlink might be used for the different areas, depending on whether or not frequencies which can be used over a wide area are available.
In some countries, the presenter uplink and downlink are also in the aeronautical VHF band (this is the case, for example, in Malta), and the frequencies use do vary significantly between countries. If you are in an area where the local radion station has a travel plane or helicopter, why not have a tune around and see what you can find and post a comment to let us all know.
Tuesday 17 February, 2009, 20:38 - Licensed
Posted by Administrator
My couple of previous posts concerning reception of BBC World Service English language programmes on short-wave in Europe led me to wondering whether there wasn't a more elegant solution to the problem of identifying which frequencies to tune to at any given time of the day.Posted by Administrator
As it happens, every 6 months, the majority of international broadcasters get together and sit down to negotiate and co-ordinate their HF frequency usage for the coming 6 months at a conference known as the High Frequency Co-ordination Conference. The resulting plans (know as the Winter and Summer seasons) are published on the web. So with a little ingenuity and a few spare hours, Wireless Waffle proudly presents:
* The 'find a frequency in a given language, for a particular broadcaster (or both) analysis tool' *
(catchy name isn't it?!)
It works like this: You can select broadcasts in a particular language, or by a particular broadcaster in which case you will be presented with a list of transmissions currently on-air (or on-air at a time you select) today for that broadcaster together with a map of the world showing where those frequencies are being transmitted from. Using this list you can try tuning to those transmitters most local to you (or for fun those more distant) to see what you can hear.
Alternatively you can select a broadcaster AND a language in which case you will receive a list of all frequencies and times for that broadcaster in that language for today, highlighting those which are currently on-air with a map showing where those frequencies which are on-air are being broadcast from. It sounds more complicated than it is - go and try it!
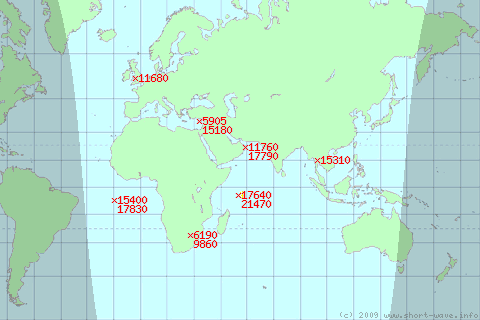
To help, regions in daylight and darkness are also shown. Generally speaking if you are in an area of darkness, look for stations also in darkness which are transmitting on low frequencies (say 10 MHz - 10000 kHz - or less). If you are in an area of daylight, look for frequencies also in daylight (over 10 MHz or so).
Happy listening.
Wednesday 21 January, 2009, 16:56 - Pirate/Clandestine
Posted by Administrator
Posted by Administrator
 Various forums and logging sites around the web have reported that short-wave pirate station Premier Radio International was recently raided. Their transmitters and studio equipment were apparently taken. Premier Radio operated on 6265 kHz on Sunday mornings from Ireland and according to the reports the Irish spectrum regulator, ComReg, received a complaint of interference from the UK spectrum regulator Ofcom which forced them into action.
Various forums and logging sites around the web have reported that short-wave pirate station Premier Radio International was recently raided. Their transmitters and studio equipment were apparently taken. Premier Radio operated on 6265 kHz on Sunday mornings from Ireland and according to the reports the Irish spectrum regulator, ComReg, received a complaint of interference from the UK spectrum regulator Ofcom which forced them into action.Such a raid on pirate broadcasters is not unheard of, though a 'cease and desist' letter is often sent to the operator first to warn them that they are at risk of being 'boarded'. Short-wave stations, however, are raided much less frequently than their FM pirate counterparts who lose transmitters on a regular basis. One of the reasons for this is that it can be much more difficult to identify the location of a short-wave transmitter. The other is that interference tends to be caused outside the country in which the transmitter is located - hence the need for the collaboration between Ofcom and ComReg.
There are, however, many short-wave pirate stations that operate in and around 6200 to 6400 kHz on Sunday mornings, and many of them operate from Ireland. So the question is, what is it about the use of this frequency that Ofcom found so objectionable that they felt the need to get ComReg to take such drastic action.
 The answer might lie in the particular use of frequency in that part of the radio spectrum. Frequencies from 6200 to 6525 kHz are allocated internationally to maritime mobile services. Within this range, certain spot frequencies have been set aside at an international level, through the International Telecommunications Union (ITU) Radio Regulations for certain specific uses. These frequencies are:
The answer might lie in the particular use of frequency in that part of the radio spectrum. Frequencies from 6200 to 6525 kHz are allocated internationally to maritime mobile services. Within this range, certain spot frequencies have been set aside at an international level, through the International Telecommunications Union (ITU) Radio Regulations for certain specific uses. These frequencies are:* 6215 (actually 6215 to 6218) kHz - allocated for distress and safety communications (analogue)
* 6268 (actually 6267.75 to 6268.25) kHz - allocated for distress and safety communications (narrow band direct printing - NBDP)
* 6312 (actually 6311.75 to 6312.25) kHz - allocated for distress and safety communications (digital selective calling - DSC)
* 6314 (actually 6313.75 to 6314.25) kHz - allocated for maritime safety information (using NBDP)
Clearly, given the safety related nature of the use of these frequencies, it makes sense to avoid them as far as possible to avoid causing interference where it really is not welcome. However, avoiding them does not just mean not transmitting on those spot frequencies. Typical AM transmitters occupy 5 kHz either side of the centre frequency on which they are transmitting. Also the spot frequencies themselves refer to transmissions with typically a 2 or 3 kHz bandwidth. So, to avoid interfering with 6215 kHz which actually uses frequencies from 6215 to 6218 kHz for example, AM transmissions on a centre frequency ranging from 6210 to 6223 kHz should be avoided. This might immediately raise the question as to why Ofcom have not complained about Italy's Mystery Radio who have used 6220 kHz for a very long time or Radio Cairo which uses 6270 kHz between 16:00 and 18:00 GMT every day, but certainly gives credence to claims that Radio Caroline's use of 6215 kHz in the late 1980s could have caused interference to safety-of-life services. With this in mind, the diagram below illustrates which frequencies within the range 6200 to 6400 kHz can be 'safely' used (in blue) without causing interference to these safety related services.
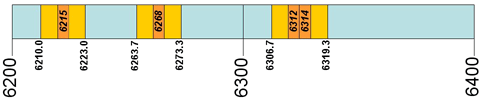
 Interfering with any legitimate radio user is not to be condoned, however safety services such as these are not the best of bedfellows. I am sure that many pirates listen to the frequency they intend to use before turning their transmitters on, assuming, that is, that they have sufficient flexibility in their choice of crystals to allow them to find something relatively free. Choosing a frequency that deliberately interferes is, though, clearly a bit mad. So Radio King on 6215 kHz, Radio Malaisy on 6310 kHz and Radio Altrex who use both 6265 and 6310 kHz - be warned - you might be next to be sunk.
Interfering with any legitimate radio user is not to be condoned, however safety services such as these are not the best of bedfellows. I am sure that many pirates listen to the frequency they intend to use before turning their transmitters on, assuming, that is, that they have sufficient flexibility in their choice of crystals to allow them to find something relatively free. Choosing a frequency that deliberately interferes is, though, clearly a bit mad. So Radio King on 6215 kHz, Radio Malaisy on 6310 kHz and Radio Altrex who use both 6265 and 6310 kHz - be warned - you might be next to be sunk.Whilst we're on the subject of frequencies not to choose, much of the HF spectrum is littered with transmissions that sound like this. These are NATO transmissions using their HF radio protocol known as STANAG 4285 and are therefore most definitely military in nature. Avoiding any frequency on which these noises can be heard would also seem to make sense too... otherwise it might be torpedos away.